The Growing Threat of Vulnerabilities
Explore the ever-increasing importance of vulnerability management in cybersecurity as threats grow exponentially. Learn about the...

Latest Articles

Explore the ever-increasing importance of vulnerability management in cybersecurity as threats grow exponentially. Learn about the...

The need for global solutions that simplify complexity has never been greater. We've spent over 15 years becoming the trusted...

In today's digitally connected world, the importance of a robust and reliable wireless network cannot be overstated.
%20(1).jpg)
Explore the unchanging facets of cybersecurity—from human nature to growing complexity and targeted vulnerabilities.

Navigate the digital landscape with resilience! Explore effective responses to cyber threats. Learn from real-world incidents,...

We spend more money than ever before, but the compromises keep growing, and the cost of these compromises keep increasing. What...
Password manager LastPass cyber-attack - our blog: how was the hacker able to gain access for a second time and what lessons can...

Businesses need to balance their investment across the five pillars identified by the NIST framework to reach cybersecruity...
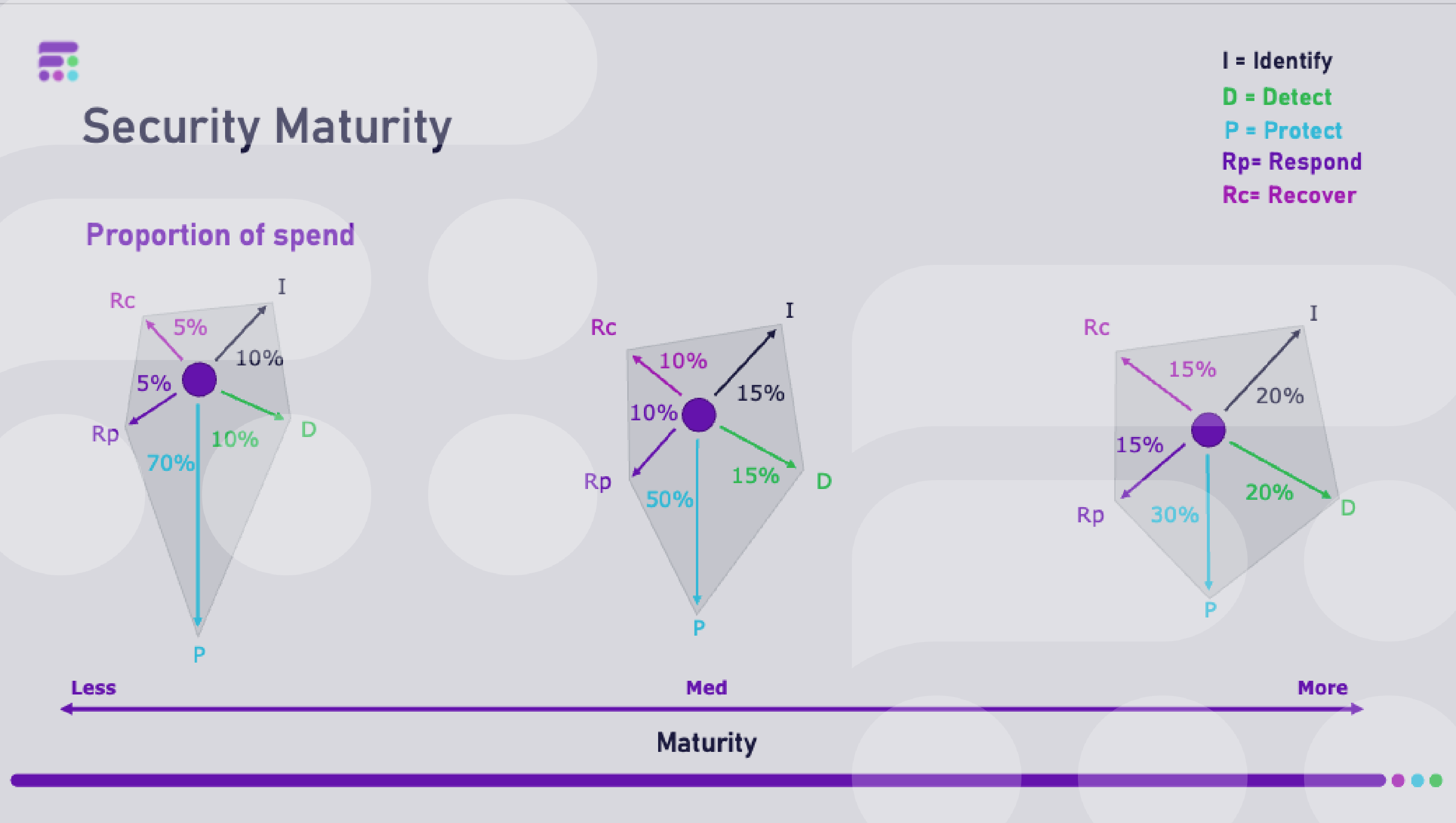
By balancing spend across the five areas identified by the NIST framework will improve cybersecurity maturity.

The Government-backed Cyber Essentials scheme can improve your companies cybersecurity. We are a trusted and experienced...